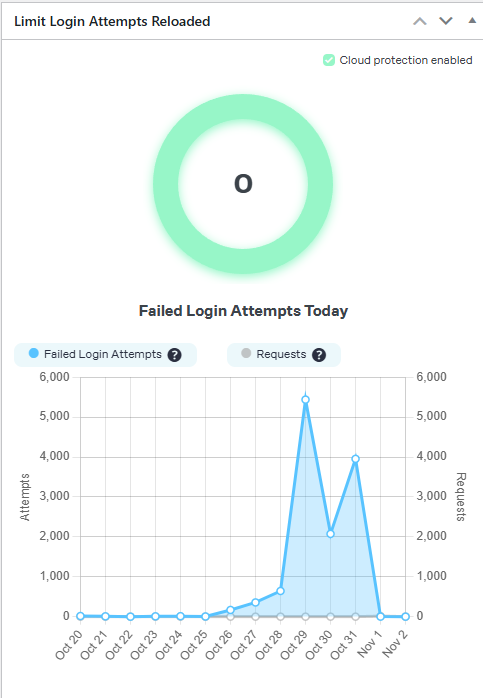
Hosting your own WordPress site is not for the squeamish. However, if you’re like me and you like full control of your site and have the means to host it, why not? It can take a lot of work, considering that foreign adversaries will try to brute force their way into the login page. I have seen in one day close to 6,000 failed login requests, which sounds kind of ridiculous when you think about what is on this server. There really isn’t anything of value just my thoughts and ideas but they try anyway. At least the bots do.
In this article, I will cover why people try to brute force their way into a WordPress site and what the reasoning behind it is. I will also cover briefly some statistical analysis of the offending countries and what you can do about it. As I write this, I will assume that you are using Linux and that you are fairly familiar with some Linux administrative responsibilities. I will not be providing you any step-by-step instructions on what you need to do, as that will come in a different article. This article is just to provide you, the reader, an idea or overall concept for stopping brute force attacks.
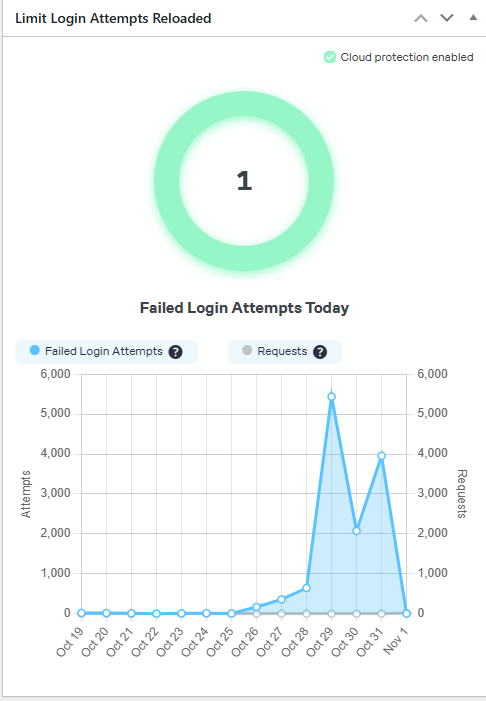
WordPress sites are a particularly attractive target because they power over 40% of all websites, and many owners use weak passwords, outdated plugins, or don’t implement basic security measures. For this article and to show you, I have used one of my servers to prove the point. As you can see from the image above, in just one day the server had almost 6,000 failed login attempts. While it is a waste of time for the would-be intruder since I do have server key authentication and the server just drops the connection as soon as you try to connect without a key it is still a waste of bandwidth and resources for the server. But I wanted to prove the point for this article, at least for those who don’t understand the concept.
Why do they do it?
There are many reasons why people or bots rather try brute forcing their way into a site. Here is a list of the most common ones:
Financial motives: Installing malware to steal credit card information or login credentials, using the site to distribute spam or phishing emails, redirecting traffic to malicious sites for ad revenue, holding the site for ransom (demanding payment to restore access), or using server resources for cryptocurrency mining.
SEO manipulation: Injecting hidden links to boost rankings of other sites they control, creating doorway pages that redirect to their content, or hijacking the site’s established authority and traffic.
Resource exploitation: Using the server as a bot in DDoS attacks against other targets, leveraging bandwidth and storage for hosting illegal content, or creating a foothold to attack other sites on shared hosting.
Malicious intent: Defacing sites for ideological or political reasons, causing disruption or reputational damage to organizations, or simply demonstrating technical capability or vandalism.
Strategic access: Building networks of compromised sites for future attacks or gathering data for identity theft or corporate espionage.
Using Plugins To Prevent Brute Force Attacks
The beauty of using WordPress is that you have many different options and plugins for thwarting brute force attacks. WordPress has many different plugins that you can use to limit failed logins. While many of them do a good job, upgraded or paid plugins are typically better. Here are some examples of plugins that I use. For instance, Wordfence Security is used to provide two-factor authentication. WPS Limit Login is a simple plugin that limits logins and provides captcha authentication, although WPS will not provide you certain features without the upgraded paid plugin. There are many more, and I will list them below for you, but these are just some of the more popular ones:
- Wordfence Security – One of the most comprehensive options, includes login attempt limiting, two-factor authentication, firewall, and real-time threat detection
- iThemes Security – Offers brute force protection, two-factor authentication, and locks out users after failed attempts
- Sucuri Security – Provides login security hardening, malware scanning, and post-hack security actions
- All In One WP Security & Firewall – User-friendly interface with login lockdown features and captcha options
- Limit Login Attempts Reloaded – Lightweight plugin focused specifically on blocking excessive login attempts
- WPS Limit Login – Simple plugin that limits login attempts and adds captcha verification
- Jetpack Security – Includes brute force protection along with other security features (requires Jetpack account)
- WP Cerber Security – Specializes in anti-spam and brute force defense with geographic restrictions
- BulletProof Security – Comprehensive security with login security and idle session logout
- LoginPress – Focuses on login customization but includes security features like login attempt limits
Fail2Ban Protection
In addition to using some of the WordPress security plugins, I also use fail2ban. What is fail2ban? It is a server-level security tool that monitors log files for suspicious activity, like repeated failed login attempts, and automatically blocks the offending IP address by updating your firewall rules.
How does it work? Fail2ban works by monitoring system logs for specific services and checks for patterns that indicate attacks. It uses regular expressions to extract information from those logs. When it detects too many failed attempts by a specific IP address within a specific amount of time, it will temporarily or permanently ban the offending IP address.
Fail2ban can protect multiple services simultaneously. You can use it to protect your proprietary web application, WordPress, and SSH. It does send out emails about banned IP addresses, but it also automatically unblocks IP addresses after a set period. Of course, this is all configurable in the configuration file, which I will cover in another article.
The main advantage of using fail2ban over WordPress plugins is that it stops attacks before they even reach the WordPress application, reducing server load. It also allows you to protect all services at once. You don’t need different methods for different applications or server services.
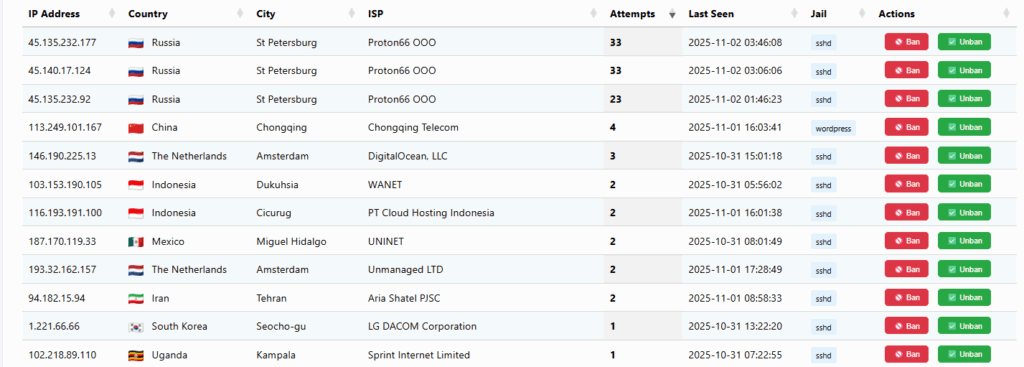
Offending Countries
While I will not go into this in great detail, it is interesting to note that the most offensive countries for brute force attacks will be listed below in an image. Out of all the countries, Russia shows up as the winner of the contest. This is typically due to many different factors, such as large pools of compromised computers that can be used as botnets, plentiful technical talent and cybersecurity experts, and hosting infrastructures that are sometimes very lenient about abuse complaints. There are other reasons, such as legal and enforcement factors, economic factors, and geopolitical factors. Combine all these reasons, and you get a country that is heavily active in brute force attacks.
It is worth noting, though, that brute force attacks can come from many different countries worldwide. Even if you see a Russian IP address, it is possible that the attacker is using a VPN (Virtual Private Network) to route traffic from some other country through the VPN, which is located in Russia. Proxy servers are another possibility, as they relay traffic through intermediate servers, hiding the true source.
In some cases, hosting providers ignore abuse complaints and don’t keep detailed logs, making it attractive for attackers to rent servers from them, and these hosting companies may be located in Russia. One thing is for certain: in my experience, the offending IP addresses that show up in my logs are predominantly from Russia.
Conclusion
If you plan on hosting your own WordPress site, you should consider at minimum using WordPress plugins. They are easy to install and very efficient. Keeping these plugins updated will minimize the potential that your site could become compromised by a would-be attacker. It is worth mentioning that using WordPress plugins does have a downside to them. WordPress plugins do add overhead to the server, as the plugins have to monitor every login attempt within the application causing additional use of CPU cycles, memory usage and bandwidth consumption.
However, if you have the knowledge and feel comfortable configuring a service like fail2ban on your server, then I would highly recommend it. Using fail2ban will stop the attacks before they even get to the WordPress application, which comes with its own advantages. Using this service will save CPU cycles, memory, and most importantly bandwidth, as the server doesn’t have to waste these resources processing malicious requests. Your site will remain fast even during such attacks since your traffic is being filtered at the firewall level. Using both doesn’t hurt either, as it adds additional layers of security to keep your server running efficiently and securely, keeping your failed authentications to a manageable number, if not eliminating them entirely.